Zero Trust Network Access (ZTNA)
Table of contents
Access verification from each individual user for applications
- Security of internal resources from the public
- Preventing possible breaches against data protection
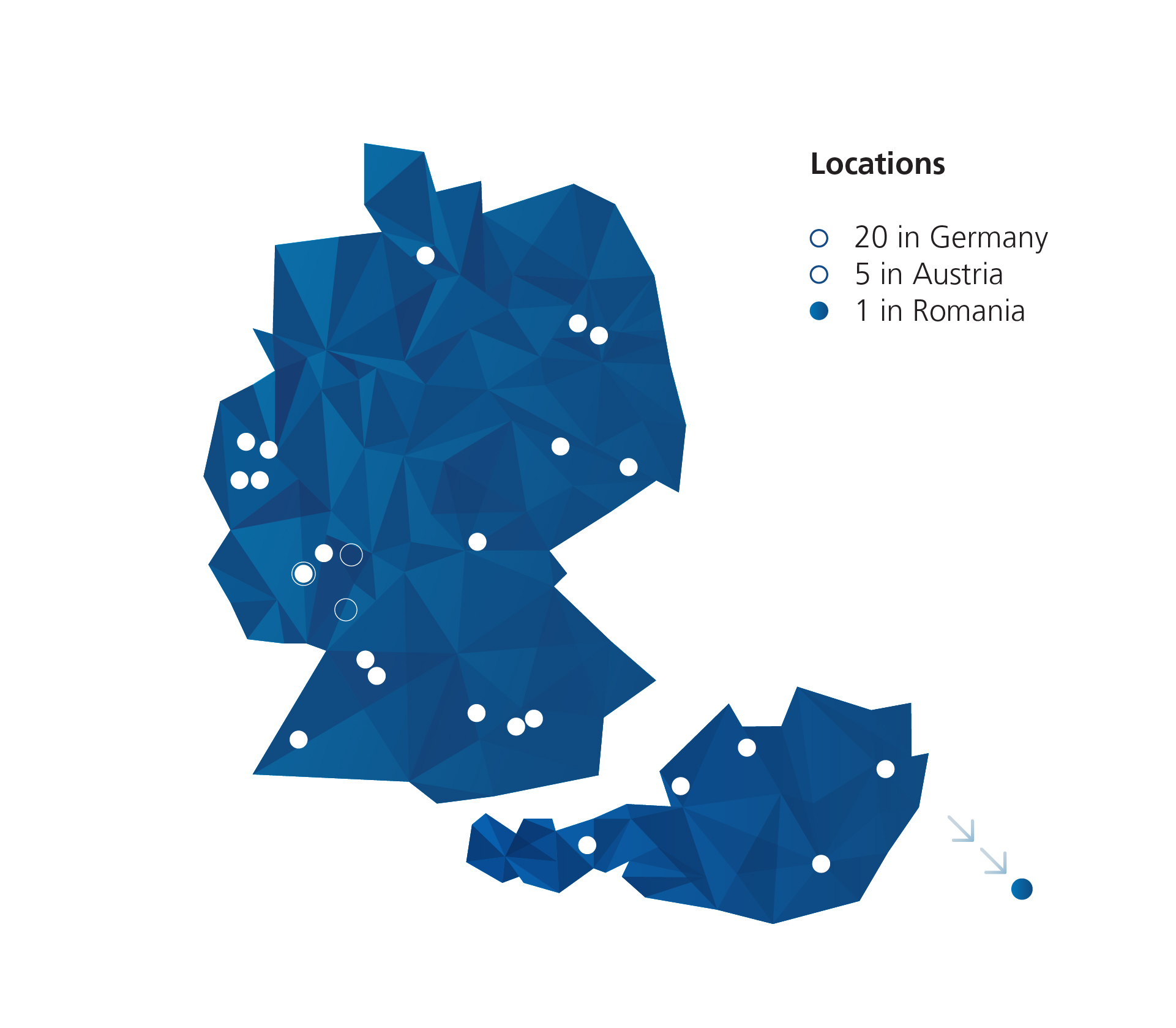
All important info at a glance