House of Security
The ultimate protection for your IT-environment
An increasing rate of threats demands better and better protective measures, permanent monitoring and a good emergency plan. The House of Security by Medialine offers all of that. It is built on the foundation of our Consulting Services, on which our bundled Security Portfolio can be found, of which you can choose the elements custom fit for yourself. Our certified SOC/CERT team continuously monitors the systems. The roof of our House of Security is formed by our Managed Services, with which you will always stay up to date. Don´t leave your environment unprotected, trust on our expertise.
Managed Security Services:
Protects against rain and threats: The Managed Security Services form the roof of the House of Security. Through regular penetration testing, scheduled meetings, monitoring, and maintenance, we ensure the security of our clients' IT infrastructure.Learn more now!schliesen
SOC/CERT Team:
Two teams, two tasks: Prevention and intervention. Our Security Operations Center team is responsible for continuously and automatically examining logs for current threats. If danger is imminent, the Computer Emergency Response Team is informed and immediately initiates countermeasures, cleans systems and performs analyses.Learn more now!schliesen
Network Security:
Defend your company against malware, ransomware, phishing, and other cyber threats. Our comprehensive security solutions—including Email Security, Managed NDR Service, Network Access Control (NAC), and SASE (Secure Access Service Edge)—ensure effective protection for your network and data.Learn more now!schliesen
Cyber Security Awareness:
95% of cybersecurity problems are unintentionally blamed on the human factor. We take your employees out of the line of fire. With our cyber security awareness offer, we sensitize all employees in your company. In this way, we strengthen your company's human firewall and implement a sustainable security strategy in your organization.Learn more now!schliesen
E-Mail Security:
Worldwide, 281.1 billion e-mails are sent every day. Analysts expect an annual increase of at least 4.3%. Email security must not be neglected in any security strategy. With our offerings, products and solutions, we protect your e-mail traffic.Learn more now!schliesen
Security Services:
With our Security Services, we effectively identify vulnerabilities, conduct penetration tests, and perform security audits and specialized tests for specific applications. We protect your systems with individual consulting and personal security services from our IT security experts.Learn more now!schliesen
Endpoint Security:
The way employees work has changed dramatically. Home office, working on the train or in Internet cafés has become the standard. Users use a wide variety of end devices, such as laptops, mobile devices or tablets. Most attacks occur via an unprotected end device and spread from there to the entire network. We show you how to protect all endpoints in your organization.Learn more now!schliesen
Disaster Recovery:
Disaster Recovery is an essential part of your IT emergency management. It ensures that IT systems and data are recoverable after failures or disruptions. Without a Disaster Recovery strategy, companies enter a danger zone that can have unimaginable consequences. With our Disaster Recovery offering, you secure the trust of your customers and business partners and enable the continuity of your operations.Learn more now!schliesen
Security Consulting:
Our Security Consulting ensures that your IT systems run securely and smoothly. Our services include conducting a current state analysis, collection of ideas, and developing concepts, followed by presentations and personalized consultations. With us, you can optimize your IT infrastructure tailored to your specific needs.Learn more now!schliesen
Our portfolio in the area of security
Contact
Would you like to learn more about the House of Security or are you interested in individual components? Please contact us via our inquiry page!
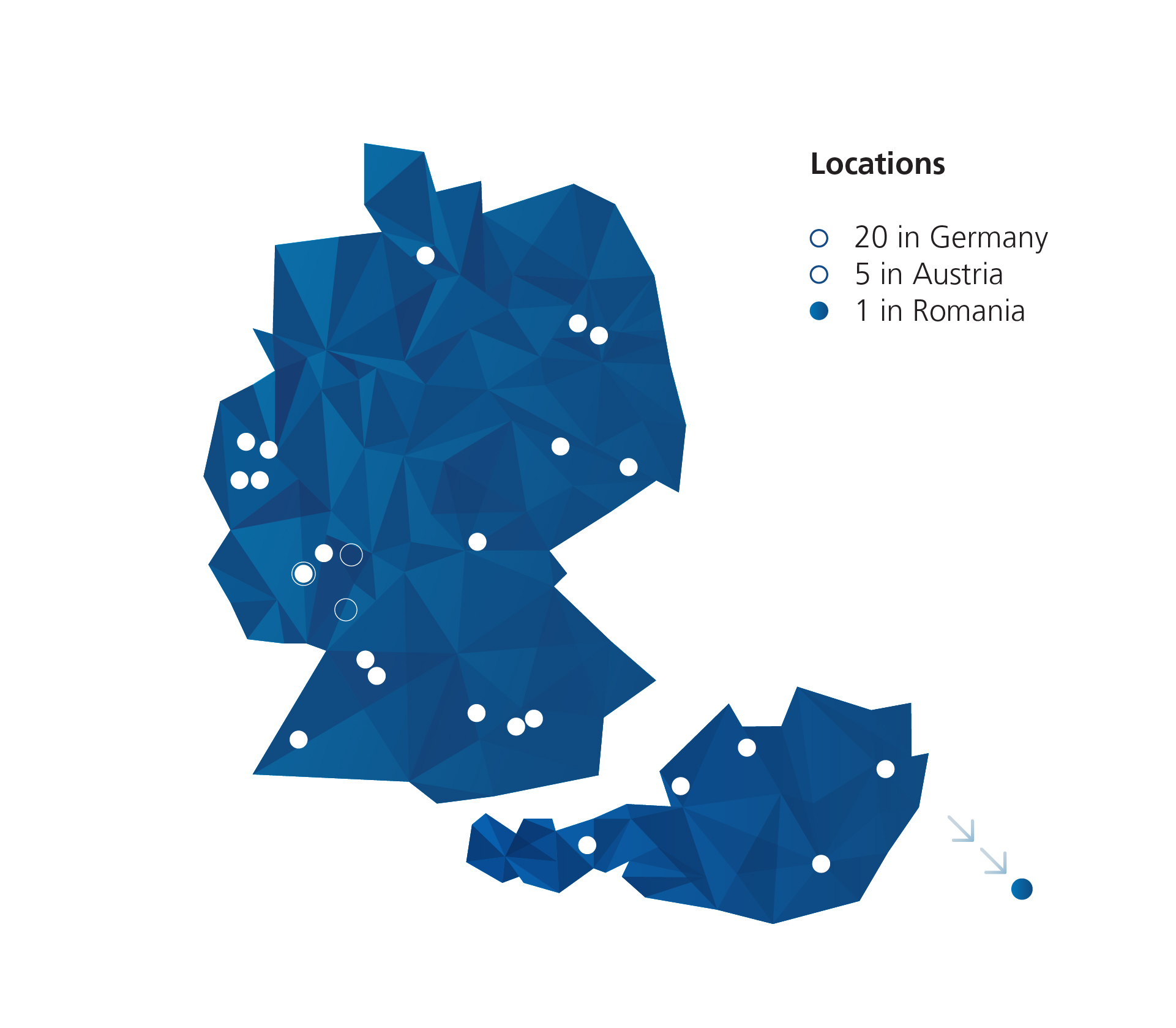
All important info at a glance